Often, when I explain what I do for a living being a management consultant, I get asked why companies hire consultants in the first place.
As much as I hate to hear it, the question makes sense: At first glance, it can be puzzling why companies wouldn’t just solve their own problems—whether it be a cost reduction effort or a new market entry—well, themselves. But there are many reasons companies really need consultants (and why I am able to stay employed working on some of the coolest challenges in the business world!).
If you’ve ever considered becoming a consultant—or hiring one—read a little more below about how we can help companies out.
They Want an Outside Eye
You know how sometimes when you’re dealing with an issue in your life, you turn to friends and family for their opinions? Companies often need this, too, especially when making tough decisions. Often times, clients have a perspective on how to solve the problem they are facing but want to make sure that what they’re thinking is correct (or that they aren’t so close to the challenge that they’re missing the obvious answer). So, they turn to consultants to come in and provide their opinion.
But this isn’t just any opinion: Because consultants often work with many different companies and may have worked through this problem in the past with someone else, they can really provide a perspective based on what they’ve seen work (or not) before. And given this experience, they can often bring new and innovative ideas or possible challenges to the table that clients probably wouldn’t have been able to see on their own.
They Need Extra Horsepower
Sometimes the problems companies need solving are really important, but they don’t necessarily have the manpower to focus on them. Companies still have to focus on their day-to-day operations, after all, and new projects typically require reprioritizing employees’ core job responsibilities. But hiring new employees to fill these gaps doesn’t always make sense either, seeing as many of these projects are one-offs. Whether it’s a cost reduction program requiring a dedicated team of six for a year or even a post-merger integration that requires a team of 100 for a month, clients might struggle to get the teams in place to do this critical work.
In instances like this, consultants basically serve as temporary, highly skilled employees. We’re not full-time employees of the company, so it is often cheaper to use us than hire someone new. Because we switch around companies often, we’re used to the fast learning curve, and onboarding us is easier. And, by using consultants, companies don’t have to pull their employees away from their actual jobs.
They Want Specialized Skills
Another, and perhaps the most common, reason that companies hire consultants is to gain access to a specialized skill set that might not exist in house. By engaging a consulting firm, you get access to a group of professionals that has skills ranging from Lean Six Sigma process design to finance organization structures. These highly specialized people would not only be expensive to hire for, but the company might not have enough work to keep said employees busy year round. But, thanks to consultants, companies can bring in that skill set on demand when they need it.
They Want a Safe Zone
Sometimes, when companies are working on a challenging problem or a controversial project, it can be hard for them to make decisions or take the necessary actions without getting wrapped up in emotions or politics. So, they bring in consultants to provide an unbiased eye and do some of the dirty work for them.
If you remember Up in the Air, George Clooney was engaged to go around the country conducting employment terminations on behalf of his clients. Likewise, clients might engage us for major restructurings or controversial projects so that they can ensure they’re handled by an external party that’s both experienced in and a bit removed from these types of activities. We can also provide the back-up and confirmation for a client that is attempting to run with a new idea that might not be well-received within an organization, without any risk to our day jobs or career
]]>Now we have science saying it: management consultants add value. A formal study, sponsored by the World Bank and using a control group of factories as well as a treatment group, quantified the results. First year economic benefits exceeded the cost of the consulting—with later years’ benefits pure gravy. (Summary in Slate, details from Nick Bloom, hat tip to Tyler Cowen.)
The project examined textile factories in India, and I was initially somewhat skeptical that the results would apply here in the United States. After reading the details, I think that American managers can learn a lot from the study. The research team began with a list of 38 good management practices (found hereon p. 40). Although they are given as specific to the textile industry, it’s easy to re-state them in terms of your own operations. For instance, “Scientific methods are used to define inventory norms for yarn” could be applied for any input material.
I strongly advise operations managers to review that list and self-evaluate. Some standards are met in virtually every factory I visit (such as “The shop floor is clear of waste and obstacles.”) Others not so much: “Customers are segmented for order prioritization.” Customers do NOT have to be served in the order in which they asked for your goods or services. First-come-first-served makes sense in some cases, but not in others. Have a reason for your prioritization system that reflects the different value of different customers, as well as operational efficiency.
The list of 38 management practices misses two areas where I see lots of opportunities: sales and pricing. Too few companies have systematic procedures to call on prospects and past customers. Too few use sales coaches to help their representatives perform better. On the pricing side, too few companies use marginal cost pricing. Instead, they either have nothing or they use an average cost estimate that fully loads in overhead. Using the wrong numbers is often worse than no number at all!
So you are running a company or a division and you wonder where you have room for improvement. First, bring in a consultant with a broad background to help you identify areas of focus. (That’s something I am good at.) Next, bring in expertise to focus on the areas most ripe for improvement. That might be your first consultant or it might be a specialist, say in sales training or cost accounting. Third, evaluate those results. Fourth, hit the next opportunity for improvement. Along the way, pat yourself on the back for taking your company to higher levels of profitability.
There are many benefits to the NIST Cybersecurity Framework. Through being neutral, broadly applicable, vetted by industry, and engaging to stakeholders, the Framework can reduce time and expense of starting an information security program and also reduce risk within current programs by identifying areas for improvement.
Neutral and Broadly Applicable
“The thing that we like about the NIST Framework is that it is neutral,” said Christman. “It’s neutral to mission of organization, to industry, and to data type.”
Although it can be used with specific data types or objectives in mind, the Framework is a much broader approach to security. Therefore, its benefits can be realized by a variety of organizations, such as hospitals, civilian federal agencies, educational institutions, defense agencies, commercial enterprises, and more.
“The other thing that we like about the Framework is that it’s neutral to threat factor,” Christman continued. “It could be a trusted insider threat, an advanced persistent threat from a nation state, or a malicious hacker. The threat factor is really not the issue. Regardless of mission, industry, data type, or threat factor, your organization can improve its security posture.”
Vetted by Industry
The Framework is also beneficial because it meets industry-vetted criteria. According to the Information Technology Industry Council (ITI), a high-tech trade association based in Washington, D.C., an effective cybersecurity effort should:
- Leverage public-private partnerships and build upon existing initiatives and resource commitments
- Reflect the borderless, interconnected, and global nature of today’s cyber environment
- Be able to adapt rapidly to emerging threats, technologies, and business models
- Be based on effective risk management
- Focus on raising public awareness
- Focus on bad actors and their threats
“The Framework is the right approach because it hits almost all of those guiding truisms,” said Danielle Kriz, Director of Global Cybersecurity Policy at ITI. “It’s globally workable and it leverages already existing standards and best practices that were developed by industry.”
Engaging to Stakeholders
The NIST Framework helps organizations communicate their cybersecurity requirements with stakeholders, including partners and suppliers. It is a good way to start a discussion with technical and non-technical stakeholders to further the security posture of organizations.
“The beauty of the Framework is we can drill down into the finite details. But at a very high level, I could explain what it means to a business person in a line of an agency or an educational institution, and help them understand what needs to happen because it can be explained in plain English,” Christman said. “We can use this Framework to connect the stakeholders – the people with access to money, people, and resources – and connect the technical, policy, and governance issues.”
]]>0 – Don’t know
1 – Initial (Activities are ad hoc/chaotic/undefined)
2 – Repeatable (Activities established / level of discipline and adherence)
3 – Defined (Activities are defined, documented, standardized)
4 – Managed (Activities are measured by quality, improved, and integrated)
5 – Optimized (Continual Service Improvement (CSI) is adopted / activities are mature)
No matter how you rate it, if you don’t have the data to tell you where you are in this model, you are only guessing. After establishing your baseline performance metrics, it is strongly recommended to perform assessments on a regular basis, typically every 12 months, to ensure progress in the areas needing improvement.
In the following paragraphs we’ll provide an overview for:
- What is an Organizational Assessment and Why You Should Conduct one
- Who Should Conduct it and What are the Qualities of a Good Organizational Assessment Team
- How Long Will it Take to Conduct Your Organizational Assessment and How Much Will it Cost
- Who Will Use Your Organizational Assessment including How to Manage it
- Why Should You Choose Consult Our Source as your Assessment team
1. What is an Organizational Assessment and Why You Should Conduct one.
An organizational assessment (OA) can be defined as a standard process for obtaining valid information used to determine key organizational strengths, weaknesses, opportunities, and risks. Four areas that are essential to include in the assessment are Customers, People, Technology, and Processes.
An OA is conducted to demonstrate areas of competence, improvement, and possible risks, as well as to help support investment and restructuring decisions. It differs from other types of evaluations because the objective of an assessment is to understand the performance of an organization, not the performance of a project, a program, or a policy. An assessment with a “Live Person” allows you to customize and tailor the questions, making it meaningful to your organization so the assessment becomes the Voice of Staff (VOS). An off-the-shelf tool should not be used, as it is ‘cookie cutter’ and not tailored to fit your organization.
Many organizations ask, “How are we doing?” but are not sure how to get the answer. OA’s are a tool that answers this question – telling you how you’re doing, what you’re doing well and why you might not be performing the way you would expect. An organizational assessment is like a physical exam – in this case it is your organization undergoing a “physical” to identify strengths and weaknesses; and areas which need to be improved, modified or strengthened.
The value in conducting assessments across the four areas of Customers, People, Technology, and Processes provides the following:
- Determine effectiveness of current processes including any gaps and/or overlaps as well as Identify resources that the organization can use to effectively improve its performance
- Customers – customer satisfaction ratings
- People – right people in the right position; move/align personnel to thrive and succeed
- Technology – Internal systems, manual/automated processes, and structure (new environments, changing technology)
- Process – modify/integrate current; add new; retire existing/outdated
- Identify an organization’s strengths and weaknesses
- Interviews of personnel at various levels in any/all areas of the IT organization in support of the internal functions of the entire company
- Generates evaluation information, which then becomes a valuable experience-based input in future planning, establishing of priorities and resource allocation;
- Furnishes financial data to justify the need for additional resources
- Provide a ‘report card’ to investors and stakeholders with information about the organization’s performance
- Generate information that will be useful in planning and decision-making like strategic decisions: Should you grow/merge/shrink; or change your mission; or offer new services
- Prioritize and respond to needs that should be addressed through specific actions to change an organization’s performance
- Whether in pre or post change, an assessment identifies organizational gaps, risks/issues and helps to determine what needs to be done to plan for a process change, move through the process, or if the change was successful
2. Who Should Conduct it and What are the Qualities of a Good Organizational Assessment Team.
A key part of the planning for an OA is to determine if it will be conducted internally (self-assessment), externally (by contracting an external assessment team), or through a combination of both internal and external resources. There are advantages and disadvantages of each type of team:
If the assessment is conducted INTERNALLY:
- Advantage: greater ownership of the process
- Drawback: greater commitment of staff time: RISK of BIASED OPINIONS; time to learn evaluation skills and time to conduct the evaluation; FEAR of ‘ASSESSING ONESELF OUT OF A JOB’; time and commitment of staff causes higher internal costs
If the assessment is conducted EXTERNALLY:
- Advantages: Less use of staff resources; UNBIASED PERSPECTIVE; IDENTIFIES TRUE VOICE of STAFF; High organizational evaluation experience; Lower internal costs (time and resources)
- Drawbacks: Higher initial external cost; Less ownership within the organization
The team – external, internal, or a mix of both – should have:
- Credibility: Recognition from the main stakeholders and members of the organization, while having the right balance of authority, responsibility, insight and knowledge of the organization.
- Technical know-how: Understanding of the OA approach, knowledge about the organization’s programs and services, and data analysis skills.
- Objectivity: Ability to balance the perspectives of different people.
- Communication skills: Ability to communicate the results of the OA in a manner easily understood by all parties.
- Interpersonal skills: Ability to interact with all parties in a sensitive and effective manner and ability to work as part of a team.
- Availability: Availability to conduct the OA and willingness to commit time to working on it.
3. How Long Will it Take to Conduct Your Organizational Assessment and How Much Will it Cost.
An organizational assessment is a commitment of time and energy. It is difficult to estimate how long it should take, as the length of the process depends on a number of variables:
- The number of strategic areas (as related to the organization’s mission) you wish to assess
- The type of data you need and its accessibility
- The availability of staff to be involved in the process
These factors will affect the duration of the process. In addition, you might want to consider the depth of the data collection that is possible within the time frame that you have to complete the OA. With these considerations, it may take a few weeks to any number of months.
The cost of an organizational assessment is not strictly determined monetarily. The total cost also includes staff members’ time (opportunity costs), the technology involved, and access to information. It also depends on who conducts the assessment.
An externally-conducted assessment will seem more expensive until you consider the points above including staff members time (continuing their current job while conducting the assessment verses only participation). The cost of an assessment also depends on the number of issues that are included and how deep the assessment is supposed to go.
4. Who Will Use Your Organizational Assessment including How to Manage it.
Prior to conducting an OA, you will want to identify the audience for the Assessment. The audience will determine the scope of the OA as well as the expected outcome. You will also be able to identify the audiences’ expectations. You will need to communicate with the audience throughout the OA process so that they have opportunities to validate preliminary findings and conclusions.
There are two types of audiences:
- Inside your Organization: Your senior officials and/or Board of Directors will find the results very useful in their strategic management or organizational change efforts. It will also help management and staff improve decisions or understanding as related to roles and responsibilities.
- Outside your Organization: If there are donors or investors, the results allow them to better understand the effects of their investments on your organization.
Managing your OA, whether it is performed internally or externally, will require a team. There are a couple of key roles that help to ensure the assessment is successful.
- The strategic role provides guidelines and directions, and oversee overall quality. Strategic responsibilities are more conceptual.
- The operational role conducts the data collection, analysis and reporting. Operational responsibilities are more hands-on
The number of individuals included in the assessment will be important. Enough people are needed to provide a range of views, but not too many that it will be difficult to make decisions. Ultimately, the results of your Organizational Assessment will provide you the data needed to create a Roadmap for the future success of your Organization and ensure that you know your organization is running as you expect, provide quality products/services and plan for growth
5. Why Should You Choose Consult Our Source as your Assessment team.
Consult Our Source is a boutique firm that specializes in performing organizational assessments. We quickly become the Trusted Advisor of the organizations that we work in. This creates a level of comfortability for participants across all levels of the organization to get the true Voice of Staff (VOS).
We have over 40 years of combined experience, work diligently to provide quality over quantity, and commit to utilizing strong industry standardized methodologies.
We operate efficiently and customize each assessment to fit the need of your organization with low overhead costs to ensure competitive rates that fit your budget.
We compile the data and provide it in multiple formats for all management levels so that it is easy to determine the next steps for your organization. i.e. executive summary, detailed assessment reports, and a summary of recommendations with a roadmap to success.
Contact us today to schedule a call and demo.
To the success of your organization,
Pam Karagines
Director of Business Development
[email protected]
www.consultoursource.com
Office Voice: 415.919.9241
Fax & International: 415.632.3237
We are a Minority Owned Small Business with MBE-NMSDC, NGLCC , SBA, GGBA, CPUC. SAM certifications
]]>Configuration Item (CI) – Examples of CIs include individual business requirements, documents, software, models, and plans inside a configuration management system.
Configuration-management system (CMS) – This system oversees the life of CI’s through enabling elements of identification, change management, and audits.
Configuration-management database (CMDB) – a collection of CI’s organized within a CMS
The CMS is created and maintained to avoid errors from incompatibilities with other CI’s.
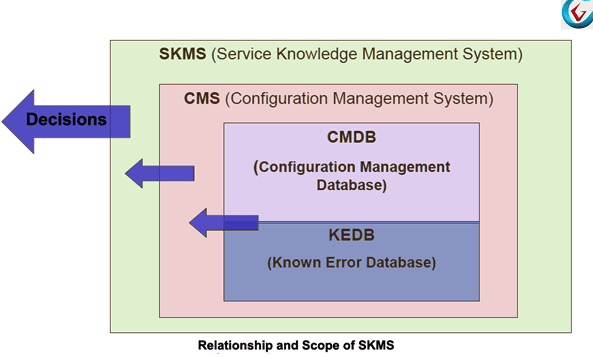
What does ‘incompatibilities with other CI’s’ mean?
I’m going to be using a parent and child analogy to demonstrate the importance of adequately constructing a CMS. Think about your great, great, great grandparent. To create offspring, there had to be several ‘compatibilities,’ from that individual to manifest the beautiful person you are now. Well, people (in this case) are the CI’s, and your family tree is the CMDB. If you implement a software piece three generations ago and decide to purchase another piece of software today, you’d better make sure it’s compatible. Otherwise, you’ve got three generations of CI’s to worry about altering.
In a seasoned CMDB, there will be professionals to establish these CI relationships and give a baseline view of the structure in a process called visual relationship mapping. This process is huge for change management, problem and incident management, and even resource management.
Importance of the service desk in knowledge management
- The ability to identify impacted CIs for every change, including downstream dependencies
- Ability to complete a risk assessment
- Discovery of potential change conflicts
- Minimized downtime for impacted assets
- A document of complete historical data for individual CIs and related records
Here’s how to use this information!
The great news is, some professionals know how to apply these practices for you! IT Consultants knowledgeable in ITIL will have a great understanding of what it takes to implement or improve an existing CMS.
The CMDB’s ability to discover IT assets using the service desk, combined with ITIL best practices, is a great way to understand how your CIs are dependent. The visual relationship mapping is responsible for the more thorough incident, problem, and change management, all of which are super important for IT Service Delivery.
]]>NIST is the National Institute of Standards and Technology, a unit of the U.S. Commerce Department. Formerly known as the National Bureau of Standards, NIST promotes and maintains measurement standards. It also has active programs for encouraging and assisting industry and science in developing and using these standards.
The frequency and intensity of cyberattacks are continually increasing, but there is hope. There are a few Cybersecurity industry compliance requirements. Still, I’d call them more ‘protocols’ since they are always growing and evolving to adapt to new security risks.
What are the data breach risks?
According to the 2020 Data Breach Investigations Report
Errors definitely win the award for best-supporting action this year. They are now equally as common as Social breaches and more common than Malware and are genuinely ubiquitous across all industries. Only Hacking remains higher, which is due to credential theft and use, which we have already touched upon. In Figure 14, you can see that since 2017, Misconfiguration errors have been increasing.
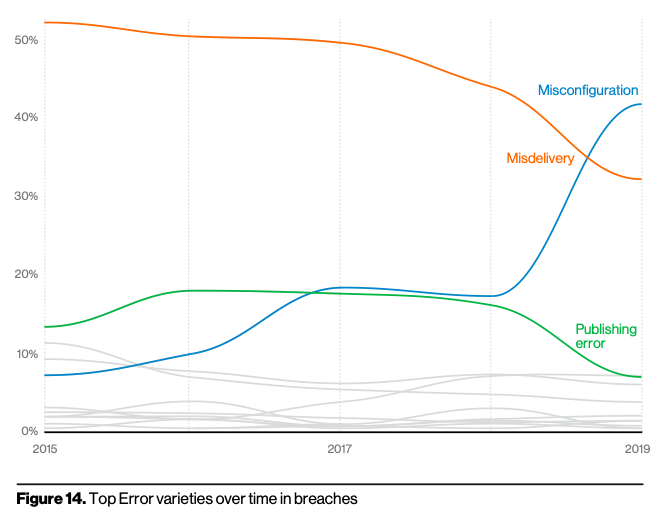
The fact that we now see errors becoming more apparent in other industries could mean we are getting better at admitting our mistakes instead of simply sweeping them under the rug. Of course, it could also mean that since so many of them are caught by security researchers and third parties, the victims have no choice but to utter “mea culpa.” A security researcher has become the most likely Discovery method for an error action breach by a significant amount being over six times more likely than it was last year.
What is compliance?
Compliance is defined as “the action or fact of complying with a wish or demand.” In IT, this must be distinguished as a practice that establishes risk-based controls to PROTECT the privacy, integrity, and accessibility of possessed information.
There are several well-known regulatory standards, including the Health Insurance Portability and Accountability Act (HIPAA) and the Payment Card Industry Data Security Standard (PCI DSS). Many of these can overlap in any IT centered business
How to create a risk assessment plan
The First step is to identify where your security vulnerabilities are – this is what will determine where compliance needs to be improved.
To create a risk assessment plan, you must:
- Identify all of your firm’s information systems, networks, and information that they access.
- Assess the risk level of each data type and determine where high-risk data is stored, transmitted, and collected.
- Analyze the risk by using the risk = (likelihood of breach x impact)/cost formula.
- Determine to transfer, refuse, accept, or mitigate the risk.
You want to continually monitor new threats to respond to them before they inflate into a problem.
IF YOU DON’T RESPOND TO A KNOWN VULNERABILITY, YOU CAN BE SUED FOR NEGLIGENCE!
Okay, So How Do I Get Cybersecurity Compliant?!
Understanding and outsourcing Cybersecurity tasks are commonly referred to as CSaaS or Cybersecurity as a Service. Looking for this service can be daunting, and you don’t have to go through the process alone. You might consider hiring a consulting company such as
Consult Our Source
It can relieve a lot of the operation strain out of transforming your company into a compliance abiding machine!
]]>Luckily when it comes to that time (and every business experiencing growth gets there) when you need to manage a customer relationship program or need some help identifying services you could offer, there is a path for you. Using the Information Technology Infrastructure Library (ITIL) frameworks, you can quickly implement industry-standard PLANNING, SUPPORTING, and DELIVERING the type of service you want to see in your startup!
ITIL isn’t just a one-time event that will help your company. You’re not running a get rich quick scheme. It’s more of a Service Management Way of thinking and behavior for your IT. Really what you get is a seasoned approach to running any business that involves technology to administer their services.
Big company? There are frameworks for that.
Small company? There are frameworks for that.
Evolving company? There are frameworks for that.
If the pattern wasn’t visible enough, there is an ITIL framework for any company using technology since it’s absolutely non-prescriptive.
“Okay, but how can it help MY startup?”
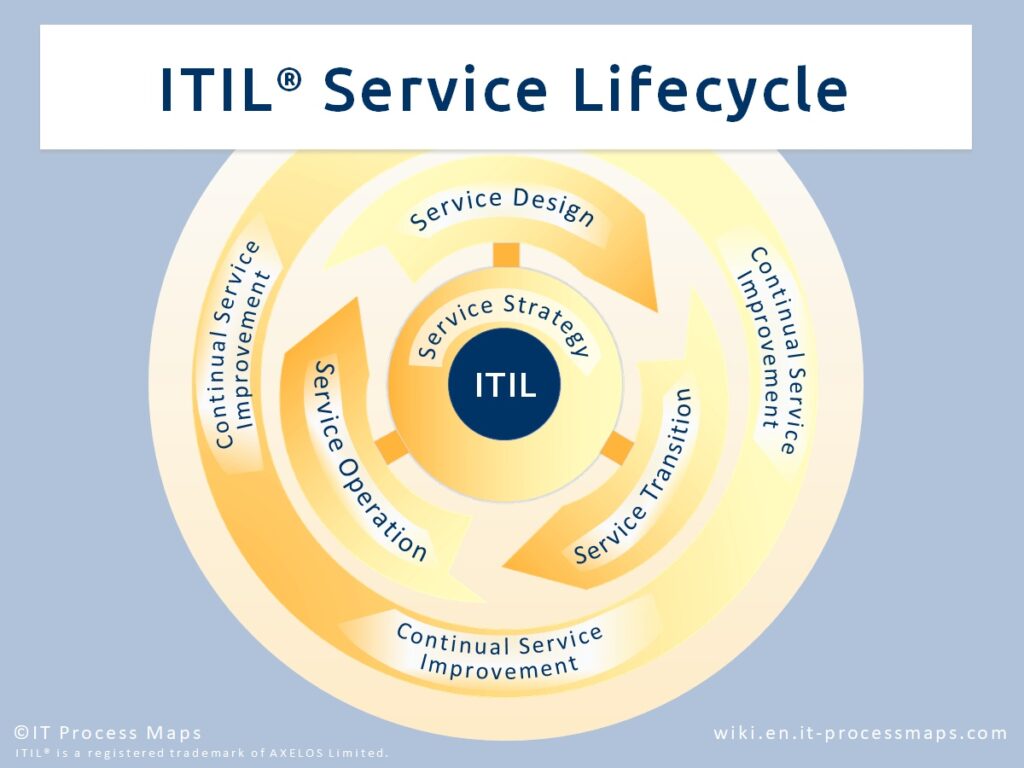
ITIL: The ITIL Service Lifecycle). – Source: https://wiki.en.it-processmaps.com/index.php/Main_Page
(I’m glad you asked!)
1. Strategy
What do I get from a Service Strategy?
- You get to identify your customer base
- Solidify the services customers need
- Solidify the services you can provide
Service Strategy is the core of your entire framework and for good reason. By understanding and improving the services your customers need, and the services you provide to them, your startup experiences a sort of Existential Self-Discovery. Who am I? What am I here to do?
2. Design
If Service Strategy is the “Who am I and what am I here to do” question, then Service Design is the “How am I going to achieve what I am here to do” matter. Design is where customer satisfaction/expectations play a tyrant. Effective and efficient designing of supporting processes is applied here for the most cost-effective route to please the tyrant.
3. Transition
Service Transition is the fun part; this is where you begin to implement your freshly designed services to your customer base in a CONTROLLED and efficient way. This phase must remain as controlled as possible to minimize reported incidents!
4. Operation
Service Operation is the phase where your startup gets to sit back and focus on providing service to customers with a robust fire-fighting style support system. You have a dedicated team monitoring your successes and failures, problems, and incidents. Essentially, your startup will have the capacity to keep service-related fires under control with proper Service Operations.
5. Continual Service Improvement
You always want to keep your eyes open for new technologies and processes that would aid in providing value to your startup and your customers – and this is the time phase to focus on just that. Service Improvement had better be in every service provider’s vision, but if it isn’t, guess what? There’s a framework for that!
How to apply ITIL to your business
There are a few things your business needs to do before you can ‘start’ living an ITIL life. You want to start where you are. Bring on an ITIL Consultant to identify and assess the processes your unique business already has and determine which best practices would benefit you most.
Therefore, putting into action ITIL, you will need to:
- Document your set business goals and objectives,
- Document what plans you currently have in place to achieve those goals
- Shortlist the relevant plans that you need to improve upon by identifying the gaps between your current services and goals for improvement
- Choose processes and best practices
- Use project management tools and techniques to put your new plans into action
- Measure and monitor the changes you have made to ensure that you are meeting goals and making adjustments to improve when you are not achieving your goals.
You can do it! Reach out to an ITIL certified consultant like Consult Our Source to learn more about how your startup can successfully integrate the Global Best Practices with ITIL.
]]>In particular, the ISO 27001 standard is designed to function as a framework for an organization’s information security management system (ISMS). This includes all policies and processes relevant to how data is controlled and used. ISO 27001 does not mandate specific tools, solutions, or methods, but instead functions as a compliance checklist. In this article, we’ll dive into how ISO 27001 certification works and why it would bring value to your organization.
The ISO first released its family of standards in 2005 and since then has made periodic updates to the various policies. For ISO 27001, the latest major changes were introduced in 2013. Ownership of ISO 27001 is actually shared between the ISO and the International Electrotechnical Commission (IEC), which is a Swiss organization body that focuses primarily on electronic systems.
The goal of ISO 27001 is to provide a framework of standards for how a modern organization should manage their information and data. Risk management is a key part of ISO 27001, ensuring that a company or non-profit understands where their strengths and weaknesses lie. ISO maturity is a sign of a secure, reliable organization which can be trusted with data.
Companies of all sizes need to recognize the importance of cybersecurity, but simply setting up an IT security group within the organization is not enough to ensure data integrity. An ISMS is a critical tool, especially for groups that are spread across multiple locations or countries, as it covers all end-to-end processes related to security.
An ISMS (information security management system) should exist as a living set of documentation within an organization for the purpose of risk management. Decades ago, companies would actually print out the ISMS and distribute it to employees for their awareness. Today, an ISMS should be stored online in a secure location, typically a knowledge management system. Employees need to be able to refer to the ISMS at any time and be alerted when a change is implemented. When seeking ISO 27001 certification, the ISMS is the chief piece of reference material used to determine your organization’s compliance level.
ISO 27001 can serve as a guideline for any group or entity that is looking to improve their information security methods or policies. For those organizations who are looking to be best-in-class in this area, ISO 27001 certification is the ultimate goal. Full compliance means that your ISMS has been deemed as following all best practices in the realm of cybersecurity to protect your organization from threats such as ransomware.
In certain industries that handle very sensitive classifications of data, including medical and financial fields, ISO 27001 certification is a requirement for vendors and other third parties. Tools like Varonis Data Classification Engine can help to identify these critical data sets. But regardless of what industry your business is in, showing ISO 27001 compliance can be a huge win. Specifically, the certification will prove to customers, governments, and regulatory bodies that your organization is secure and trustworthy. This will enhance your reputation in the marketplace and help you avoid financial damages or penalties from data breaches or security incidents.
What happens if you don’t comply with ISO 27001? If your organization has previously received a certification, you could be at risk of failing a future audit and losing your compliance designation. It could also prevent you from operating your business in certain geographical areas.
How to Become ISO 27001 Certified

Receiving an ISO 27001 certification is typically a multi-year process that requires significant involvement from both internal and external stakeholders. It is not as simple as filling out a checklist and submitting it for approval. Before even considering applying for certification, you must ensure your ISMS is fully mature and covers all potential areas of technology risk.
The ISO 27001 certification process is typically broken up into three phases:
- The organization hires a certification body who then conducts a basic review of the ISMS to look for the main forms of documentation.
- The certification body performs a more in-depth audit where individual components of ISO 27001 are checked against the organization’s ISMS. Evidence must be shown that policies and procedures are being followed appropriately. The lead auditor is responsible for determining whether the certification is earned or not.
- Follow-up audits are scheduled between the certification body and the organization to ensure compliance is kept in check.
What are the ISO 27001 Standards?
Before embarking on an ISO 27001 certification attempt, all key stakeholders within an organization should become very familiar with how the standard is arranged and used. ISO 27001 is broken into 12 separate sections:
- Introduction – describes what information security is and why an organization should manage risks.
- Scope – covers high-level requirements for an ISMS to apply to all types or organizations.
- Normative References – explains the relationship between ISO 27000 and 27001 standards.
- Terms and Definitions – covers the complex terminology that is used within the standard.
- Context of the Organization – explains what stakeholders should be involved in the creation and maintenance of the ISMS.
- Leadership – describes how leaders within the organization should commit to ISMS policies and procedures.
- Planning – covers an outline of how risk management should be planned across the organization.
- Support – describes how to raise awareness about information security and assign responsibilities.
- Operation – covers how risks should be managed and how documentation should be performed to meet audit standards.
- Performance Evaluation – provides guidelines on how to monitor and measure the performance of the ISMS.
- Improvement – explains how the ISMS should be continually updated and improved, especially following audits.
- Reference Control Objectives and Controls – provides an annex detailing the individual elements of an audit.
What are the ISO 27001 Audit Controls?

The documentation for ISO 27001 breaks down the best practices into 14 separate controls. Certification audits will cover controls from each one during compliance checks. Here is a brief summary of each part of the standard and how it will translate to a real-life audit:
- Information Security Policies – covers how policies should be written in the ISMS and reviewed for compliance. Auditors will be looking to see how your procedures are documented and reviewed on a regular basis.
- Organisation of Information Security – describes what parts of an organization should be responsible for what tasks and actions. Auditors will expect to see a clear organizational chart with high-level responsibilities based on role.
- Human Resource Security – covers how employees should be informed about cybersecurity when starting, leaving, or changing positions. Auditors will want to see clearly defined procedures for onboarding and offboarding when it comes to information security.
- Asset Management – describes the processes involved in managing data assets and how they should be protected and secured. Auditors will check to see how your organization keeps track of hardware, software, and databases. Evidence should include any common tools or methods you use to ensure data integrity.
- Access Control – provides guidance on how employee access should be limited to different types of data. Auditors will need to be given a detailed explanation of how access privileges are set and who is responsible for maintaining them.
- Cryptography – covers best practices in encryption. Auditors will look for parts of your system that handle sensitive data and the type of encryption used, such as DES, RSA, or AES.
- Physical and Environmental Security – describes the processes for securing buildings and internal equipment. Auditors will check for any vulnerabilities on the physical site, including how access is permitted to offices and data centers.
- Operations Security – provides guidance on how to collect and store data securely, a process that has taken on new urgency thanks to the passage of the General Data Protection Regulation (GDPR) in 2018. Auditors will ask to see evidence of data flows and explanations for where information is stored.
- Communications Security – covers security of all transmissions within an organization’s network. Auditors will expect to see an overview of what communication systems are used, such as email or videoconferencing, and how their data is kept secure.
- System Acquisition, Development and Maintenance – details the processes for managing systems in a secure environment. Auditors will want evidence that any new systems introduced to the organization are kept to high standards of security.
- Supplier Relationships – covers how an organization should interact with third parties while ensuring security. Auditors will review any contracts with outside entities who may have access to sensitive data.
- Information Security Incident Management – describes the best practices for how to respond to security issues. Auditors may ask to run a fire drill to see how incident management is handled within the organization. This is where having software like SIEM to detect and categorize abnormal system behavior comes in handy.
- Information Security Aspects of Business Continuity Management – covers how business disruptions and major changes should be handled. Auditors may pose a series of theoretical disruptions and will expect the ISMS to cover the necessary steps to recover from them.
- Compliance – identifies what government or industry regulations are relevant to the organization, such as ITAR. Auditors will want to see evidence of full compliance for any area where the business is operating.
One mistake that many organizations make is placing all responsibilities for ISO certification on the local IT team. Although information technology is at the core of ISO 27001, the processes and procedures must be shared by all parts of the organization. This concept lies at the heart of the idea of transitioning devops to devsecops.
When preparing for an ISO 27001 certification audit, it is recommended that you seek assistance from an outside group with compliance experience. For example, the Varonis group has earned full ISO 27001 certification and can help candidates prepare the required evidence to be used during audits. Varonis also offers software solutions like Datalert to help put an organization’s ISMS into practice.
Tips to Maintain ISO 27001 Compliance

Earning an initial ISO 27001 certification is only the first step to being fully compliant. Maintaining the high standards and best practices is often a challenge for organizations, as employees tend to lose their diligence after an audit has been completed. It is leadership’s responsibility to make sure this doesn’t happen.
Given how often new employees join a company, the organization should hold quarterly training sessions so that all members understand the ISMS and how it is used. Existing employees should also be required to pass a yearly test that reinforces the fundamental goals of ISO 27001.
In order to remain compliant, organizations must conduct their own ISO 27001 internal audits once every three years. Cybersecurity experts recommend doing it annually so as to reinforce risk management practices and look for any gaps or shortcomings. Products like Datadvantage from Varonis can help to streamline the audit process from a data perspective.
An ISO 27001 task force should be formed with stakeholders from across the organization. This group should meet on a monthly basis to review any open issues and consider updates to the ISMS documentation. One outcome from this task force should be a compliance checklist like the one outlined here:
- Obtain management support for all ISO 27001 activities.
- Treat ISO 27001 compliance as an ongoing project.
- Define the scope of how ISO 27001 will apply to different parts of your organization.
- Write and update the ISMS policy, which outlines your cybersecurity strategy at a high level.
- Define the Risk Assessment methodology to capture how issues will be identified and handled.
- Perform risk assessment and treatment on a regular basis once issues have been uncovered.
- Write a Statement of Applicability to determine which ISO 27001 controls are applicable.
- Write a risk treatment plan so that all stakeholders know how threats are being mitigated. Using threat modeling can help to achieve this task.
- Define the measurement of controls to understand how ISO 27001 best practices are performing.
- Implement all controls and mandatory procedures as outlined in the ISO 27001 standard.
- Implement training and awareness programs for all individuals within your organization who have access to physical or digital assets.
- Operate the ISMS as part of your organization’s everyday routine.
- Monitor the ISMS to understand whether it is being used effectively.
- Run internal audits to gauge your ongoing compliance.
- Review audit outcomes with management.
- Set corrective or preventive actions when needed.
ISO 27001 Quick Guide: FAQ
The process and scope of ISO 27001 certification can be quite daunting, so let’s cover some commonly asked questions.
Q: What are ISO 27001 requirements?
A: In order to earn an ISO 27001 certification, an organization is required to maintain an ISMS that covers all aspects of the standard. After that, they can request a full audit from a certification body.
Q: What does it mean to be ISO 27001 certified?
A: To be ISO 27001 certified means that your organization has successfully passed the external audit and met all compliance criteria. This means you can now advertise your compliance to boost your cybersecurity reputation.
Q: What is the latest ISO 27001 standard?
A: The latest standard is known officially as ISO/IEC 27001:2013. It was published in 2013 as the second official edition of ISO 27001. The standard was last reviewed and confirmed in 2019, meaning no changes were required.
Q: Is ISO 27001 GDPR compliant?
A: Because ISO 27001 is mainly a framework for developing an ISMS, it will not cover all of the specific rules of the General Data Protection Regulation (GDPR) instituted by the European Union. However, when paired with ISO 27701, which covers the establishment of a data privacy system, organizations will be able to fully meet the requirements specified in GDPR.
Q: What are the main similarities or differences between SOX and ISO 27001?
A: While ISO 27001 covers the general management of information and data, the Sarbanes–Oxley Act (SOX) is specific to how financial information is disclosed in the United States. Fortunately for companies who have a wide scope of data management, earning ISO 27001 certification will also help to prove compliance to SOX standards.
Q: What is the purpose of other ISO?
A: The ISO maintains a full set of standards that sit underneath ISO 27001. These all take concepts from the framework and dive into more specific guidelines of how to institute best practices within an organization.
Resources
- Green Paper on how ISO 27001 can reduce cyber risk
- Webinar on how to ensure a successful ISO 27001 audit
- Case studies about ISO 27001 compliance
No matter the size of your company or what industry you work in, gaining ISO 27001 certification can be a huge win. However, it is a challenging task so it’s important to leverage other stakeholders and resources during a compliance project. With tools like Varonis Edge, you can halt cyberattacks before they reach your network while also showing evidence of your ISO 27001 compliance.
Written by Jeff Peters @ https://www.varonis.com/blog/author/jpetters/
]]>